Certificates that are not in use by a virtual server can be added using the configuration form.
Additionally, certificates, which are in use by a virtual server, can be filtered out with the configuration form.
Viewing Certificates
The tool shows managed certificates, listed by Account, Agent, or Device Group.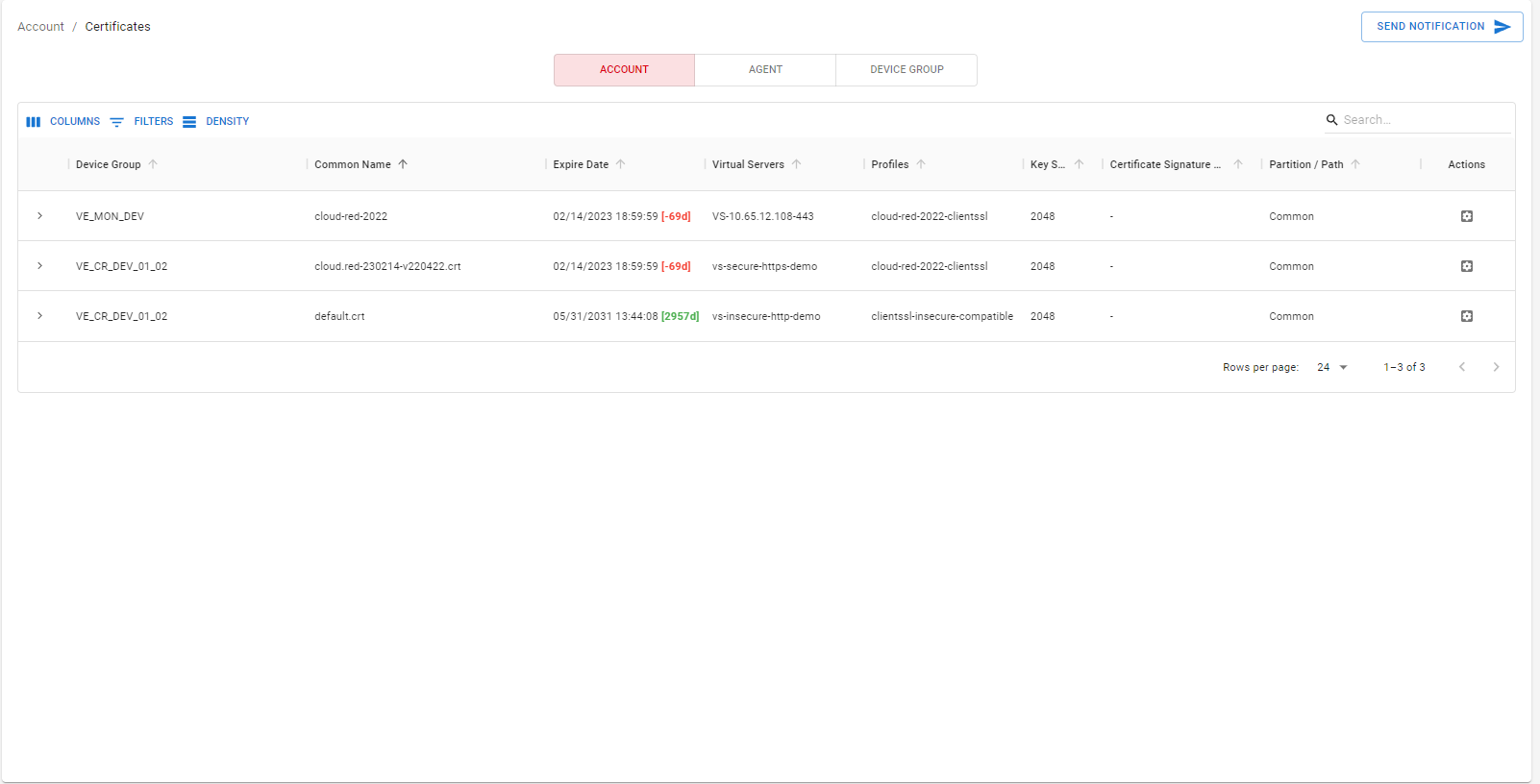
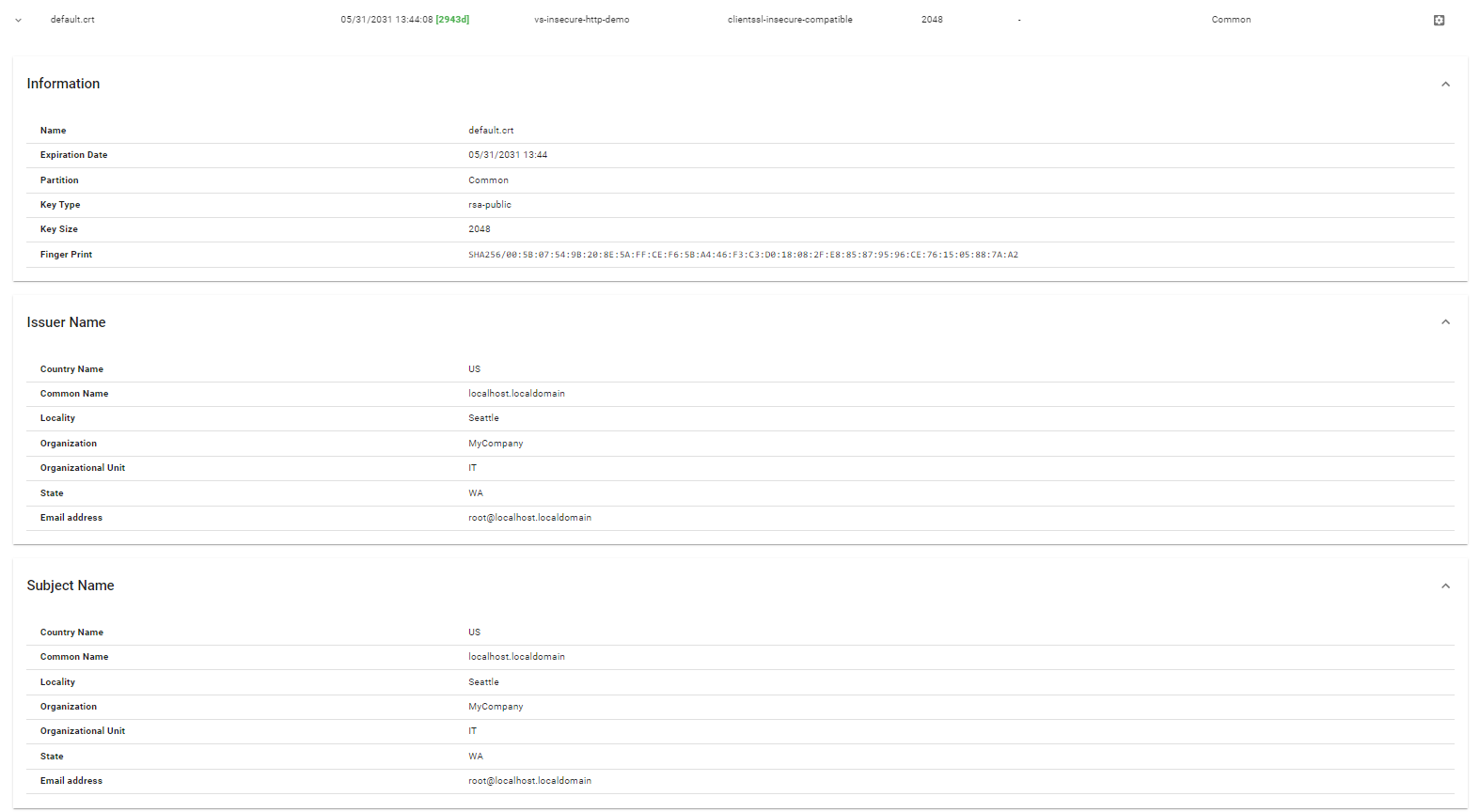
Click on the expand button of the certificate to view its detailed attributes and associated information
Configuration
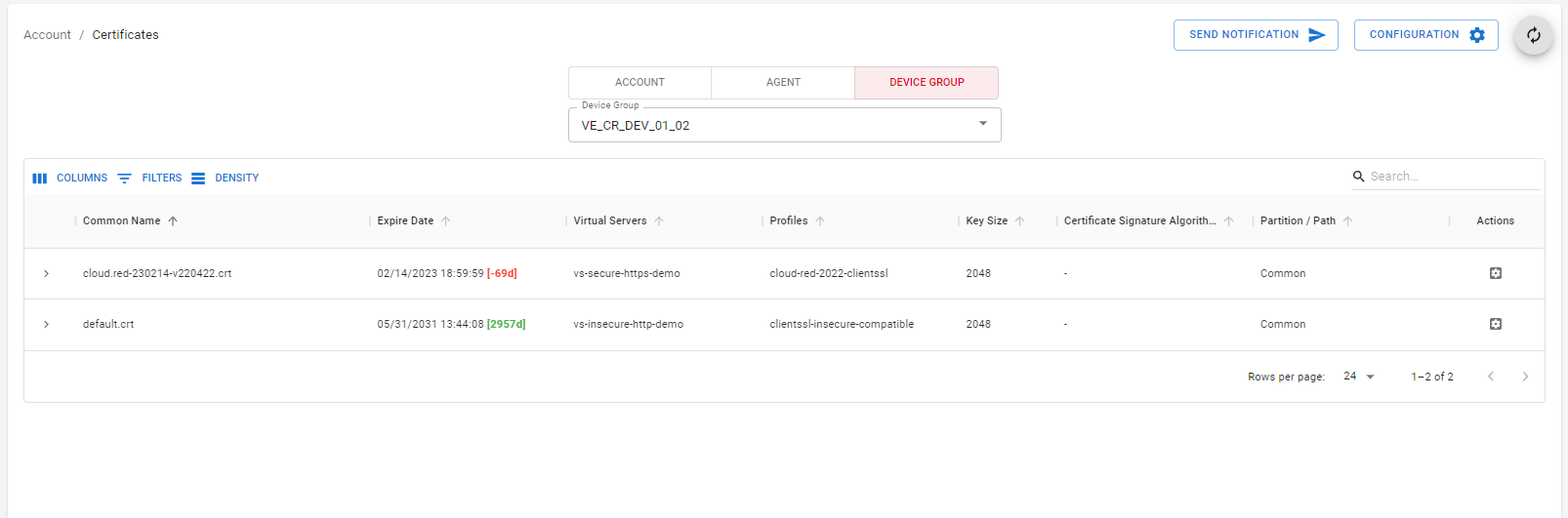
Configuration of certificates available to the tool is handled at the device group level.To modify a device group’s certificate management configuration, go to the device groups tab and select configuration in the top right corner.
Note: Access to the configuration form is also available by going to the left panel, selecting “Device Groups”, and selecting the “Certificates Configuration” option under “Actions”.
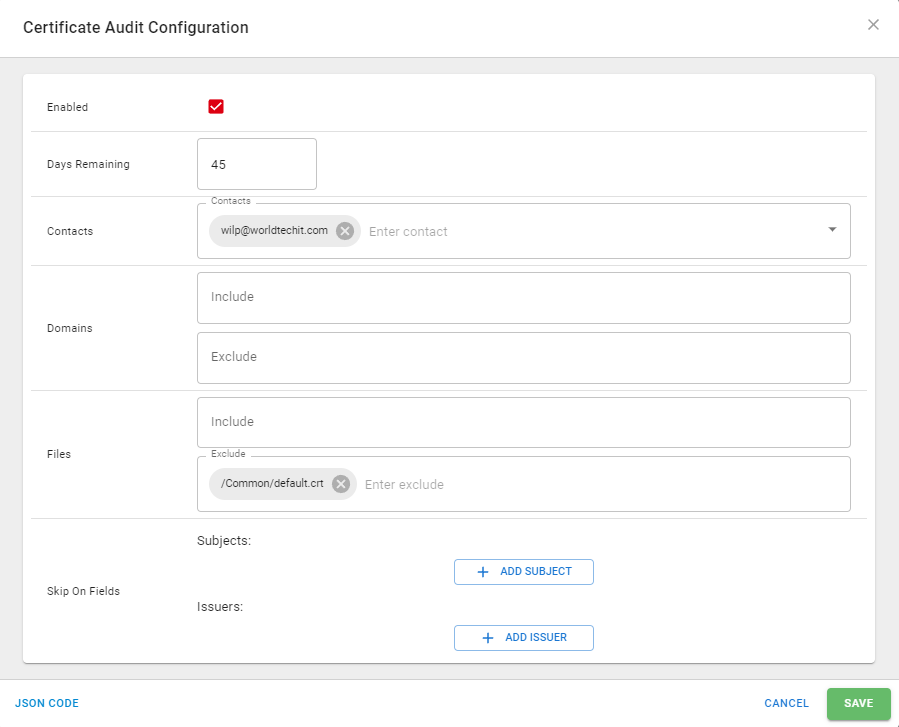
- Enabled / disable the certificate management feature (disabled by default)
- Set the ‘Days Remaining’ for a certificate’s expiration to trigger an automated notification email
- Set who will be sent automated notification emails
- Set domains to include
- Add certificates by domains, which are included in an ssl profile, but the profile is not included in a virtual server
- Please see section below regrading domain filtering syntax
- Set domains exclude
- Filter out certificates by domains, which otherwise were automatically added
- Please see section below regrading domain filtering syntax
- Set files to include
- Add certificates by file name, which are included in an ssl profile, but the profile is not included in a virtual server
- Set files to exclude
- Filter out certificates by file name, which otherwise were automatically added
- Set subjects to exclude (filter out certificates with subjects, which otherwise were automatically added)
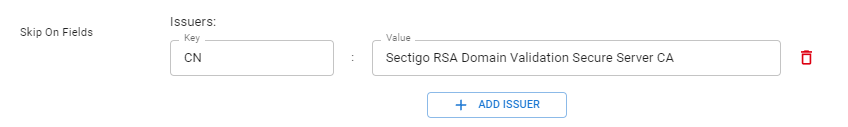
- Set issuers to exclude (filter out certificates with issuers, which otherwise were automatically added)
Changes to the configuration require the clicking of the “Save” button to commit the change.
A list of associated keys definitions are provided in the table below.
| Key | Associated field |
|---|---|
| C | Country |
| CN | Common Name |
| L | Locality |
| O | Organization |
| ST | State |
Example: To filter out certificates which have a issuer with common name “Sectigo RSA Domain Validation Secure Server CA”, the following entry would be added:
Configuration
Whether setting domains to include or exclude, domain matching the following rules:- Entries are taken as literal strings
- The literal string entries will exact match against a certificates configured domain name (wild cards are not currently supported)
- The literal string entries will match against a certificates wildcard domain name
